110,000,000,000,000 TSIT
Tesla Inu Token
We were scammed, Now we won’t let others be scammed.

Our Mission & Vision
To rid the world of scams through coordinated international collaboration

To lead the fight against scams worldwide


Technical details of TSIT
Contract Address
0x68e4992d5BDD9c7E8d43883F49123445349eE594
Token Name
Tesla Inu Token
Ticker
TSIT
Total Supply
110,000,000,000,000 TSIT
Blockchain Type
BEP20 (BNB Chain)
Decimal
18
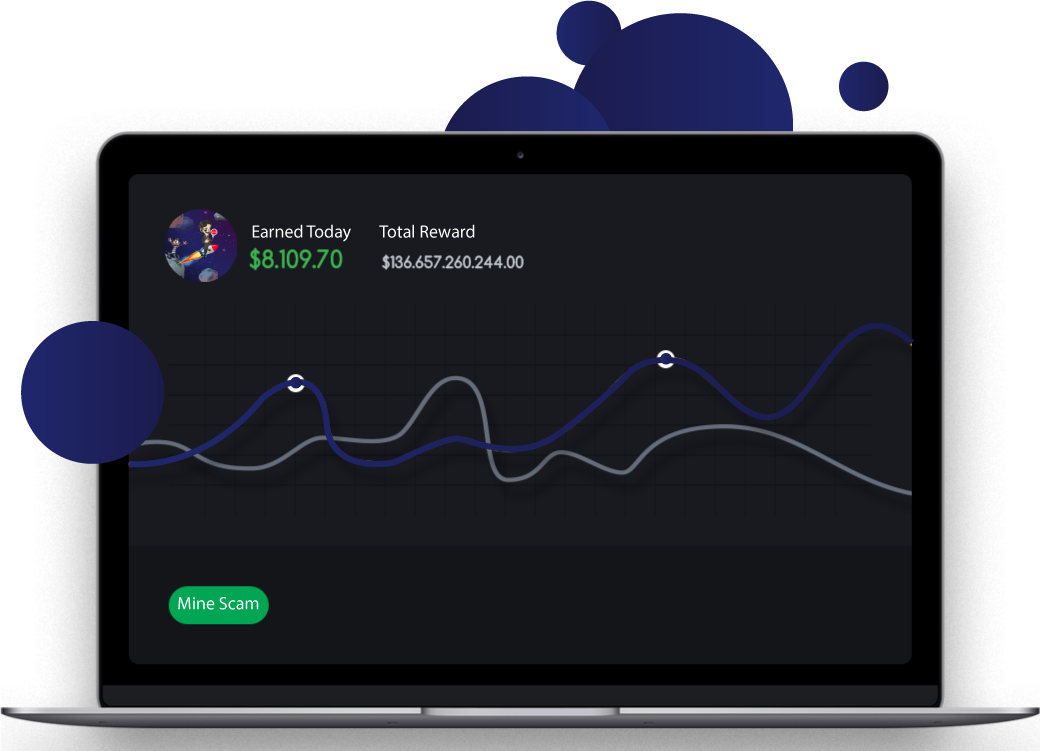
Access scam reporting and mining dashboard
Token Details (Tokenomics)

Fund Distribution


Frequently Asked Questions
-
Anyone who really wants to help the society by reporting the scam to protect the people
-
Scam Reporting Fees is the income which is given to user who submit scam report. Duplicate Scam (Previously Reported Scam won’t be considered for this income)
-
Initially TSIT will be given in your Teslainu.com website’s account wallet address. You can transfer or hold this TSIT to any other wallet or exchanges.
-
You will receive your Scam Reporting Fees once your Scam Report is verified and confirmed by Scam Miners. That will take 24 hours.
-
Scam Mining Reward is the reward which is given to only one Scam Miner who verifies maximum no of scams in 24 hours (calculation will be done between 00:00 UTC to 23:59 UTC)
-
You can earn scam mining reward if you verifies highest no of scams in give time slot (scam block). But to receive good no of scam reports to verify you must hold good no of TSIT in Scam Mining Wallet on www.teslainu.com.
Roadmap


Understanding scams
-
Market Manipulation
-
Pump And Dump Schemes
-
Rug Pulls
-
Traditional Hacking and Theft
-
Initial Coin Offering (ICO) Scams
-
Telegram Chats
-
Investment Scams
-
Loader or Load-up scams
-
Giveaway Scams
-
Email Impersonation: Spoofed Websites and Phishing Attempts
MARKET MANIPULATION
Market fraud is a deliberate attempt to influence or disrupt crypto currencies’ prices. Frequently, fraudsters deceive the markets in order to provide a favorable measure for themselves and to make quick returns.
Pre Caution: -Always learn about growth invest. Keep an eye out for prices in the real structures and market patterns in which you will should not be part of the market. portfolio and report if you see any volatility that

PUMP AND DUMP SCHEMES
The pumping and dumping system represents an individual or group effort to raise crypto currency prices so that they can sell their goods for profit.
Pre Caution: -So, there are lot of pump and dump groups who send signals for pumping of certain crypto currencies. Then they start pumping the price of crypto and take their benefits but the one who is new to signals makes a loss because he/she enters market at high. So, beware of such signals. And not to participate such activities.

RUG PULLS
Rugby draws occur when crypto developers leave the project but keep the money collected from investors. Evil actors can list new token on domain exchanges, associate it with official cryptocurrency, and raise interest rates on social media to attract investors. When enough money goes into their token, the developers scrutinize the project and work with investor funds.
Pre Caution: - The easiest way to identify a token that can be deducted is to check its total spending pools. Real tokens with strong project objectives will have tens of millions of dollars in revenue. It is very likely that a cryptocurrency with a limited liquidity pool will be drawn. Make your own calculation before investing

TRADITIONAL HACKING AND THEFT
Just as you would not share your credit card number with a stranger, keep your keys confidential somewhere safe. Scammers can use this information to hack accounts and extort money - and they will use various tactics to get investors to disclose their confidential information. Beware of phishing emails to steal sensitive information that could act as a crypto exchange or a wallet provider. The same goes for external blue promotions and unsolicited promotions from suspicious websites and fraudulent accounts. Fraudsters often impersonate celebrities or executives of large corporations, promising guaranteed and immediate profits if you do something immediately.
Pre Caution: - Never access personal or financial data via public WIFI, question about links and attachments, choose your apps wisely, turn off unwanted items.

INITIAL COIN OFFERING (ICO) SCAMS
The Initial Coin Offerings (ICO) is equivalent to the Initial Public Offering (IPO) of stock. An easy way to detect an ICO scam - or an unorganized management team - is to review the company's white paper. This document provides details on the background of the project, including strategy, objectives, and market analysis. If the company does not provide white paper, that is the red flag. ETC.
Pre Caution: - A cryptocurrency or ICO whitepaper is the basic document for that project. Companies that do not provide white paper should be avoided at all costs

TELEGRAM CHATS
Many time when you ask for support from a particular exchange team or real crypto project teams, you will start to get answers from fraudsters. You will receive random messages in the telegram about solving your issues
Warning: - One should stop responding to continuous and indifferent text messages on telegram or any other social media platforms.

INVESTMENT SCAMS
These scammers ask you to invest money to earn higher returns without financial risk, then request you to bring more people in to do the same. They often need a constant flow of new people investing in order to make money. Ponzi and pyramid schemes are great examples of investment scams
Pre Caution: - Always verify the license of the person selling the investment, verify if the investment is registered, beware of promises of high rates of return and or quick profits, be suspicious of the high-pressure sales and unsolicited offers, always ask for prospectus, consult a third-party person.

LOADER OR LOAD-UP SCAMS
Fraudsters frequently offer “loading” services on a variety of platforms. They claim to need Specific Wallet accounts with high limits, offering the victim a portion of the proceeds. These scammers use stolen credit cards on compromised accounts to perpetuate payment fraud. The end result is the victim is left with payment delinquencies after the legitimate card holder discovers the fraud, the scammer often steals any available cryptocurrencies and submits unauthorized charges on verified payment methods. Be aware, you are responsible for any payments submitted using your authentication credentials.
Pre Caution: - Be aware, you are responsible for any payments submitted using your authentication credentials. Never provide your passwords or security codes to third parties under any circumstances.

Giveaway Scams
Scammers are using social media to perpetuate giveaway scams. They post screenshots of forged messages from companies and executives promoting a giveaway with hyperlinks to fraudulent websites. Fake accounts will then respond to these posts affirming the scam as legitimate. The fraudulent websites will then ask that you “verify” your address by sending cryptocurrency to the scam giveaway.
Warning: - Be skeptical of websites or services promising high returns or unrealistic investment opportunities. If it sounds too good to be true, it usually Precaution: - send cryptocurrency to trusted third parties. Search for publicly verifiable reviews or articles involving the recipient. Watch for grammatical errors in communications or on websites. Scammers often make grammar or spelling mistakes. Research the organization thoroughly. Check consumer-protection websites and make telephone calls and send emails to verify authenticity..

EMAIL IMPERSONATION: SPOOFED WEBSITES AND PHISHING ATTEMPTS
This scam is the most common in the cryptocurrency world. Through phishing emails, scammers might impersonate representatives from popular cryptocurrency exchanges like Binance, Huobi Global, or Coinbase.
They could also impersonate Bitcoin wallets or other cryptocurrency apps. Oftentimes, they’ll issue a “security alert” in an attempt to alarm you and lure you to a fraudulent site to enter your security and account credentials. This allows them to gain access to your Bitcoin or cryptocurrency account
Pre Caution: To protect yourself, it’s a good idea to manually type in the name of the website into your browser to ensure you get to the right one. A little extra time spent to ensure your protection is worth it..